My List of OAuth 2.0 Real Interview Questions and Answers Asked Now in 2025

If you're interviewing for roles that involve user data sharing, third-party integration, or single sign-on (SSO) such as a backend developer, DevOps or SRE, a security engineer, or a mobile app developer, then OAuth 2.0 will be a key skill for interviewers to test. This is because the protocol is the cornerstone of modern internet security and open ecosystems.
I was in the same boat not long ago, so I’ve collected this list of the top interview questions and answers for 2025. This isn't just a dry list of definitions. My goal is to give you the exact strategies and practical examples you need to impress recruiters. We'll cover everything from core concepts, flows, and actual questions to critical security best practices and real-world implementation tips.
I’m really grateful to Linkjob.ai for helping me pass my interview, which is why I’m sharing my interview questions and experience here. Having an undetectable AI coding interview assistant indeed provides a significant edge.
What Is OAuth 2.0 and How Does It Work?
Definition
OAuth 2.0 is an authorization framework described in RFC 6749. It lets third-party applications get limited access to protected resources without needing the resource owner's password. Instead of sharing credentials, oauth 2.0 uses tokens. The authorization server issues these tokens after the resource owner approves access. The client then uses the access token to interact with the resource server. This protocol separates the client from the resource owner, which solves many security problems that come from sharing passwords directly. Oauth 2.0 is designed for HTTP and is not backward compatible with oauth 1.0. This framework has become the standard for secure authorization and token-based authentication in modern web applications.
OAuth 2.0 Use Cases
I see oauth 2 everywhere now, from social logins to enterprise APIs. The advantages of oauth 2 are clear: it allows secure, time-limited access to resources and supports both user and machine-to-machine scenarios. When I use "Sign in with Google" or connect a fitness app to my health data, oauth 2.0 is working behind the scenes. In my experience, oauth 2.0 makes it easy for apps to request only the permissions they need, thanks to scopes and role-based access. The use of tokens, especially access tokens and refresh tokens, means that sensitive credentials stay safe. I often register my app with an oauth provider, redirect users for authentication, handle the returned authorization code, and then exchange it for an access token. This process keeps everything secure and efficient.
Tip: Always use HTTPS, validate redirect URIs, and store tokens securely. These best practices help prevent common security issues.
The advantages of oauth 2 go beyond just security. It supports flexible authentication and authorization flows, making it a top choice for developers and companies. I always mention these points in interviews.

Why Do Interviewers Ask OAuth 2.0 Questions?
Interviewers ask about these because they want to know if I can design secure systems. They expect me to understand how authorization and authentication work together. Many companies use oauth 2 for secure access delegation. This means users can grant limited access to apps without sharing passwords. I often get questions about how the authorization server and resource server interact, or how the client gets permission from the resource owner.
I also see questions about security risks. Interviewers want to know if I understand token theft, phishing, and why some oauth 2 flows are safer than others. They might ask about the dangers of using the implicit flow or why PKCE is important. I always mention best practices like using secure storage for tokens and preferring server-to-server communication for sensitive data.
Interviewers focus on oauth 2.0 because it is the backbone of secure API access and identity management. If I can explain the roles, flows, and security best practices, I show that I am ready for real-world challenges.
One thing that helped me was learning the four main roles in oauth 2.0:
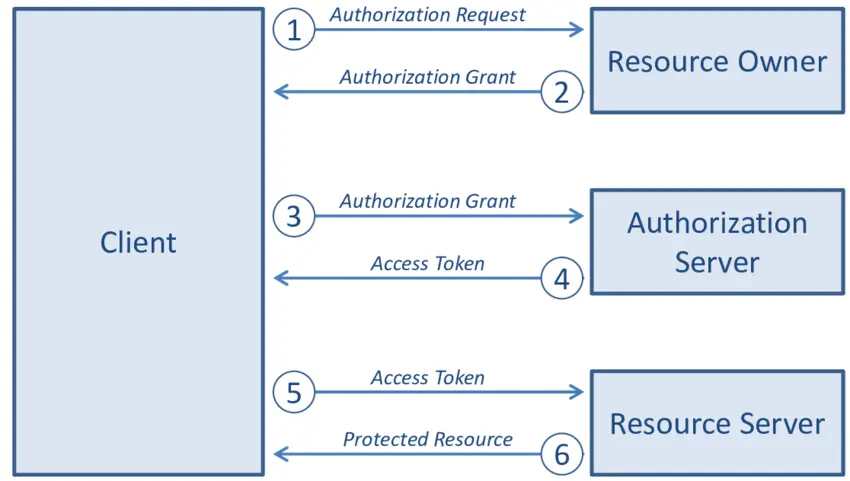
Client: App that asks for access, uses tokens, and never sees the user's password.
Resource Owner: Person who owns the data and decides what apps can access their information.
Authorization Server: Handles user login, shows consent screens, and issues access or refresh tokens.
Resource Server: Stores the data and checks tokens before sharing any information.
Top 20 OAuth 2.0 Interview Questions and Answers
I’ve divided the OAuth 2.0 interview questions into five categories, all based on real questions I've faced myself. For each one, I’ll tell you what the interviewer is really looking for, and then give you targeted solutions and sample answers for the actual questions.
Of course, these are just a handful of the many possible questions. If you want to practice answering on your own after reading this, you can use an AI mock interview platform to test yourself, where you'll find more questions to reference and practice with.
OAuth 2.0 Flows Interview Questions
Interviewers wanted to know if I understood each grant type in oauth 2 and when to use them. Here are the main flows:
Flow | Scenario | Key Point |
|---|---|---|
Authorization Code Flow | Server-side web apps | Needs client secret, secure backend |
Authorization Code Flow with PKCE | Mobile/single-page apps | No client secret, protects against attacks |
Implicit Flow | Browser-based apps (now discouraged) | No refresh token, security risks |
Client Credentials Flow | Machine-to-machine | No user, backend only |
Device Authorization Flow | Devices with limited input | User authenticates on another device |
Question:
"Explain the authorization code grant and when you would use PKCE."
Sample Answer:
In my view, the Authorization Code Grant is the most secure and core OAuth 2.0 flow, which I primarily use for web applications with a backend. Its central security principle is to move the process of obtaining an Access Token from the browser to a server-to-server exchange, ensuring the token is never exposed to the user. When my client is a public client, such as a mobile app or single-page application that cannot securely store a key, I use PKCE to enhance security. PKCE employs an extra random code for validation, guaranteeing that even if the authorization code is intercepted, an attacker cannot impersonate my app to obtain a token, thus securing the entire flow even without a client secret.
Question:
What is the difference between Authorization Code and Implicit Flow?
Sample Answer:
In my view, the main difference between the Authorization Code and Implicit flows is security and their intended use case. I consider the Authorization Code flow the standard for confidential clients like web applications with a backend. It’s a secure, server-side flow where the access token is never exposed to the browser. The Implicit flow, on the other hand, was designed for public clients like SPAs, where the access token is returned directly in the URL fragment. I now consider the Implicit flow deprecated because this exposure makes the token highly vulnerable to theft and logs. For my modern applications, I always use the more secure Authorization Code flow with PKCE, regardless of the client type.
OAuth 2.0 Tokens Interview Questions
Tokens come up in almost every oauth 2 interview questions round. I get asked about access token and refresh token differences, storage, and security. Here’s what I focus on:
Access tokens let apps access APIs for a short time.
Refresh tokens help apps get new access tokens without asking users to log in again.
Access tokens can be bearer tokens or sender-constrained tokens.
I never store tokens in local storage because of XSS risks.
Question:
"What is the difference between an access token and a refresh token?"
Sample Answer:
To me, the core difference is their purpose and lifespan. I see the Access Token as a short-lived pass for directly accessing protected resources, designed to expire quickly to minimize risk if it's intercepted. In contrast, the Refresh Token is a long-lived key used only to get a new access token when the current one expires. This two-token design effectively balances security with user convenience, preventing users from having to log in repeatedly.
Question:
"How do you securely store tokens in a single-page app?"
Sample Answer:
When it comes to securely storing tokens in a Single-Page App (SPA), my primary challenge is that SPAs are unable to securely store a client secret. My first rule is to never store tokens in localStorage or sessionStorage as they are highly vulnerable to Cross-Site Scripting (XSS) attacks. My preferred best practice is to have the SPA use a Backend for Frontend (BFF) server as an intermediary. After the BFF exchanges the authorization code for a token, it sends the token back to the browser as an HTTP-only and SameSite cookie. This approach prevents client-side JavaScript from accessing the token, completely mitigating the risk of XSS, while the SameSite attribute also helps defend against CSRF attacks.
OAuth 2.0 Security Interview Questions
Security is a huge part of oauth 2.0 interview questions. I always get questions about CSRF, token theft, and security best practices. Here’s what I cover:
I use short-lived access tokens and rotate refresh tokens.
I always validate the state parameter to stop CSRF attacks.
I pre-register redirect URIs to prevent open redirector attacks.
I never use the implicit flow for new apps.
Sample Question:
"How do you prevent CSRF in oauth 2.0 flows?"
Sample Answer:
I prevent CSRF in OAuth 2.0 flows primarily by using the state parameter. Before redirecting a user to the authorization server, I generate a unique, unguessable string and store it in their session. I then include this string in the authorization request URL. When the user is redirected back, I validate that the returned state parameter matches the one I stored. If they don't match, I reject the request. This ensures the request originated from a legitimate user, as an attacker would not be able to guess the correct state value.
Sample Question:
"What are the risks of using the implicit flow?"
Sample Answer:
In my view, the primary risk of using the implicit flow is that the access token is directly exposed in the URI fragment of the redirect URL. This makes the token highly vulnerable to being logged in browser history or server logs and can be easily intercepted by man-in-the-middle attacks or malicious scripts. Because the token is handled entirely on the client side, there is no way to securely use a refresh token, which forces users to re-authenticate frequently. For these reasons, I consider the implicit flow deprecated and always use the more secure Authorization Code flow with PKCE for my modern applications.
OAuth 2.0 Implementation Interview Questions
When I answer oauth 2.0 interview questions about implementation, I focus on real-world problems. Interviewers want to see if I can handle token management, redirect URIs, and platform-specific issues.
I encrypt tokens and use secure cookies.
I validate redirect URIs against a whitelist.
I use PKCE for mobile and single-page apps.
I check scopes before granting access.
Sample Question:
"How do you handle token storage in a mobile app?"
Sample Answer:
When I handle token storage in a mobile app, I prioritize using the platform's native, hardware-backed secure storage. For Apple devices, I use the iOS Keychain, and for Android, I use the Android Keystore System. These are dedicated, encrypted vaults designed specifically for sensitive data like refresh tokens, making them far more secure than any file or local database storage. After getting the tokens using the Authorization Code flow with PKCE, I store the long-lived refresh token in these secure systems. I keep the short-lived access token in memory for immediate use, ensuring that the most valuable credentials are never exposed on the device's file system.
Sample Question:
"What is the difference between oauth and SAML?"
Sample Answer:
From my experience, the core difference between OAuth and SAML is their purpose: OAuth is for authorization, while SAML is for authentication. I think of OAuth as a valet key, because it gives a third-party application delegated permission to access specific resources, like your photos, without ever sharing your password. In contrast, I see SAML as a digital passport used for Single Sign-On (SSO), where it authenticates your identity with a service provider by leveraging your credentials from a trusted identity provider. In short, OAuth answers the question "What can this app do?", and SAML answers "Who is this user?".
Advanced OAuth 2.0 Interview Questions
For advanced oauth 2.0 interview questions, I get asked about PKCE, JWT revocation, and new oauth 2.1 changes.
I explain why PKCE is now required for public clients.
I talk about JWT revocation with short-lived tokens and revocation lists.
I mention that oauth 2.1 removes the implicit flow and requires exact redirect URI matching.
I never store tokens in local storage for SPAs.
Sample Question:
"How do you revoke a JWT access token?"
Sample Answer:
In my experience, revoking a JWT access token is a unique challenge because JWTs are stateless and valid until they expire. I address this with a two-pronged approach. First, I set a very short expiration time, typically just 5 to 15 minutes, which minimizes the window of opportunity if a token is compromised. For immediate revocation, such as when a user logs out, I maintain a revocation list on the server. I add the unique ID of the token to this list, and my application checks it on every request. If the token is on the blacklist, I immediately reject the request, effectively invalidating it before its natural expiration.
Sample Question:
"What changes does oauth 2.1 bring?"
Sample Answer:
From my perspective, OAuth 2.1 is a much-needed cleanup and security enhancement of the original OAuth 2.0 specification. The biggest changes for me are the removal of insecure flows. The implicit grant, which exposed the access token in the URL, is now completely gone, as is the risky Resource Owner Password Credentials grant. Most importantly, PKCE is now mandatory for the Authorization Code grant, which means that even public clients like mobile apps and SPAs are now secure by default without any optional extensions. The spec also now requires an exact match for the redirect_uri, which further prevents common attack vectors.
OAuth 2.0 Interview Questions Answering Strategies and Tips
Answer Strategies
When I answer oauth 2 interview questions, I start with a clear definition. I explain the main concept, then give a real-world example from my own projects. This helps me show that I understand both the theory and the practice of authorization and security. I use a simple structure: definition, explanation, example, and trade-offs.
Common Mistakes
I made a few mistakes early on in my interview journey. Sometimes I jumped into solutions without asking clarifying questions. I also used buzzwords without really explaining what they meant. However, interviewers want me to show real understanding, not just repeat terms. That's why ignoring security details or failing to mention strong authentication can hurt my chances.
Here are some common mistakes I try to avoid:
Not asking clarifying questions before answering.
Over-committing to topics I don’t fully understand.
Using technical jargon without clear explanations.
Forgetting to mention security or authorization trade-offs.
Not sharing real-world examples from my own experience.
Practice Tips
I practice oauth 2 interview questions by working through real scenarios. I read official documentation and follow blogs from trusted sources. I also review common questions, like the difference between oauth 2 and OpenID Connect, or how to secure tokens in a mobile app.
FAQ
Besides the Authorization Code Grant, what other insecure grant types should I avoid?
You should avoid all flows that have been deprecated by the OAuth 2.1 specification. These mainly include the Implicit Grant and the Resource Owner Password Credentials Grant. The former has serious security risks because it exposes the access token directly in the URL, while the latter violates the core principle of OAuth by requiring the client to handle the user’s password. In my work, I only use the Authorization Code Grant, and I always combine it with PKCE because it's considered the most secure and universal option available today.
What is the relationship between OAuth 2.0 and OpenID Connect (OIDC)?
This is a very common question. Simply put, OAuth 2.0 is an authorization protocol, while OIDC is an authentication protocol. OAuth 2.0 focuses on "What can this client access on my behalf?", while OIDC, which is built on top of OAuth 2.0, adds the identity layer to answer the question, "Who is this user?" When a client uses the OIDC flow, in addition to getting an Access Token, it also receives an ID Token that contains the user's identity information, such as their name and email. In my projects, I always use them together: OAuth 2.0 handles the authorization, and OIDC handles the authentication. You can find the official specification here: OpenID Connect Core 1.0.
Why does PKCE make the Authorization Code Grant safe for Single-Page Apps (SPAs)?
The key to PKCE is that it solves the problem of public clients being unable to securely store a client secret. Without PKCE, if a malicious attacker intercepts an authorization code, they can use it to impersonate the client and exchange it for an access token. With PKCE, however, the client sends a randomly generated "challenge code" (code_challenge) when it requests authorization. When it's time to exchange the authorization code for a token, it must also provide the original "verifier code" (code_verifier). The authorization server then validates that the two codes match. This extra layer of defense ensures that even if the authorization code is intercepted, an attacker without the original verifier cannot complete the token exchange, protecting the security of the entire flow.

