My 2026 UBS HackerRank Test Experience: Real Questions

My UBS’s HackerRank test had quite a lot of questions. A total of 16. Aside from one coding problem and one multiple-select question, the other 14 were all single-select. Below, I will share the interview questions I encountered.
I’m really grateful to Linkjob.ai for helping me pass my interview, which is why I’m sharing my OA questions and experience here. Having an undetectable AI interview tool during the interview indeed provides a significant edge.
This article is part of the HackerRank series. If you're interested in other articles in this series, feel free to read: Microsoft HackerRank test, JP Morgan HackerRank test, Stripe HackerRank online assessment.
UBS HackerRank Test Coding Question
Coding Question: Blacklisted IPs
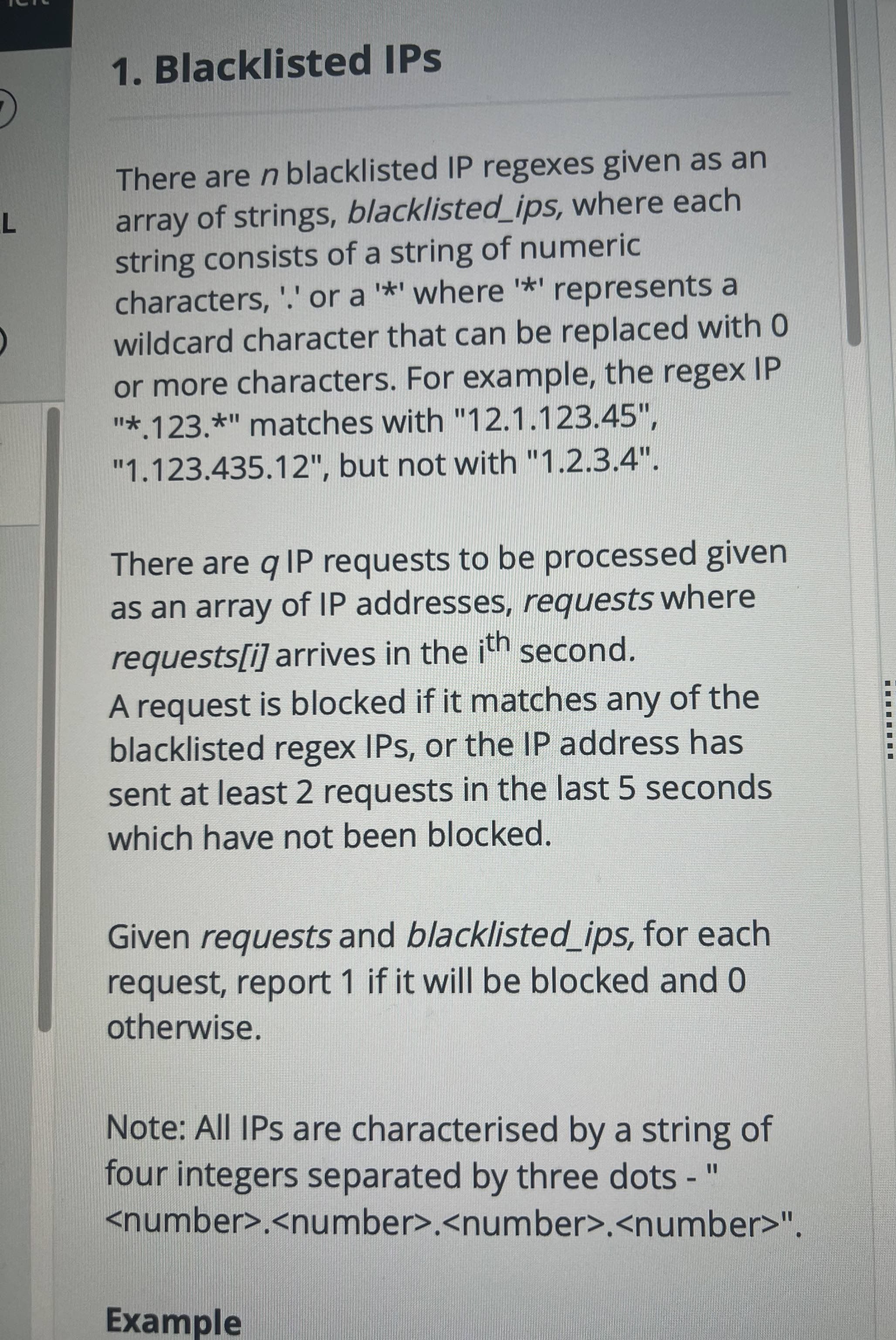
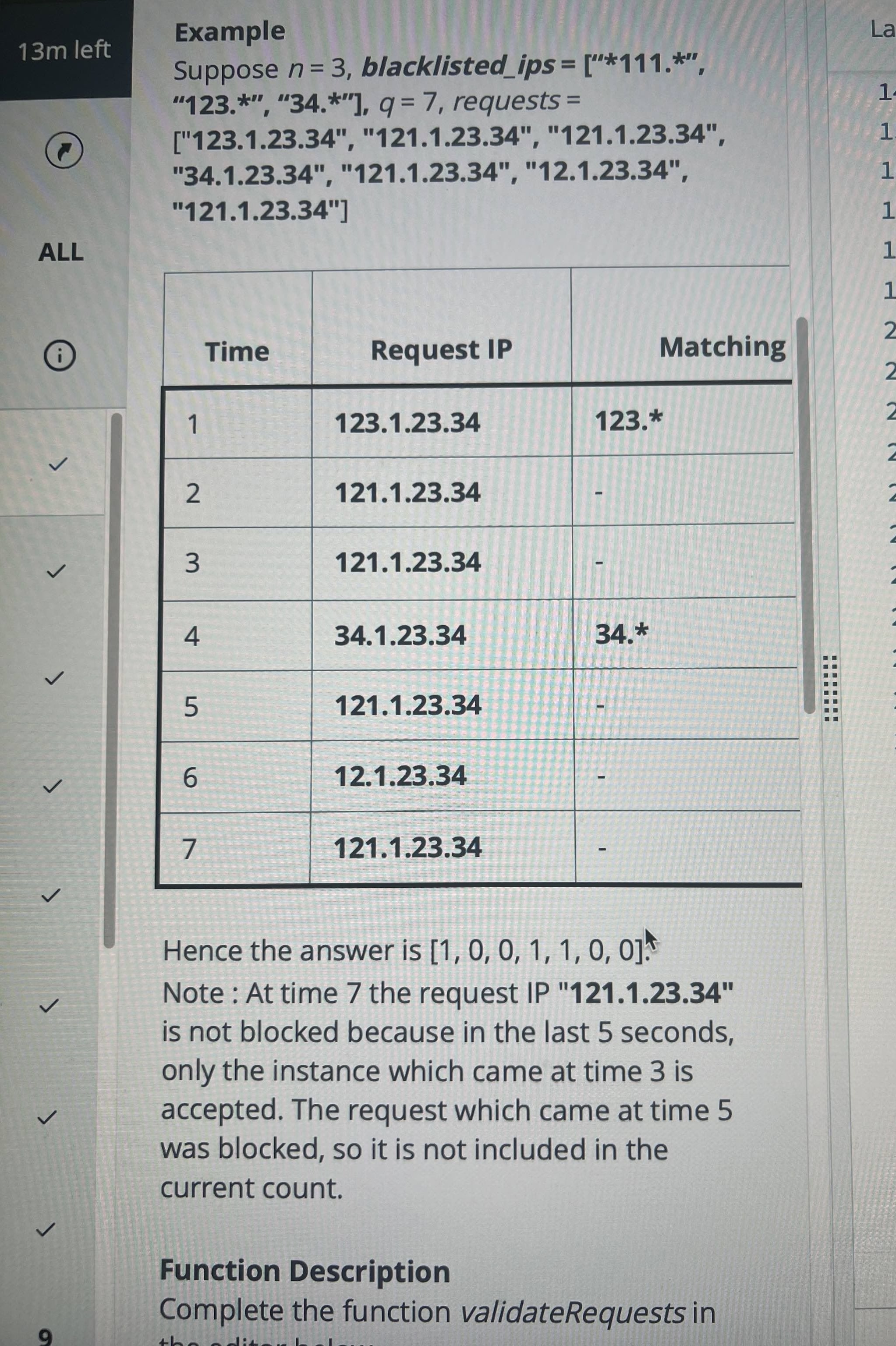
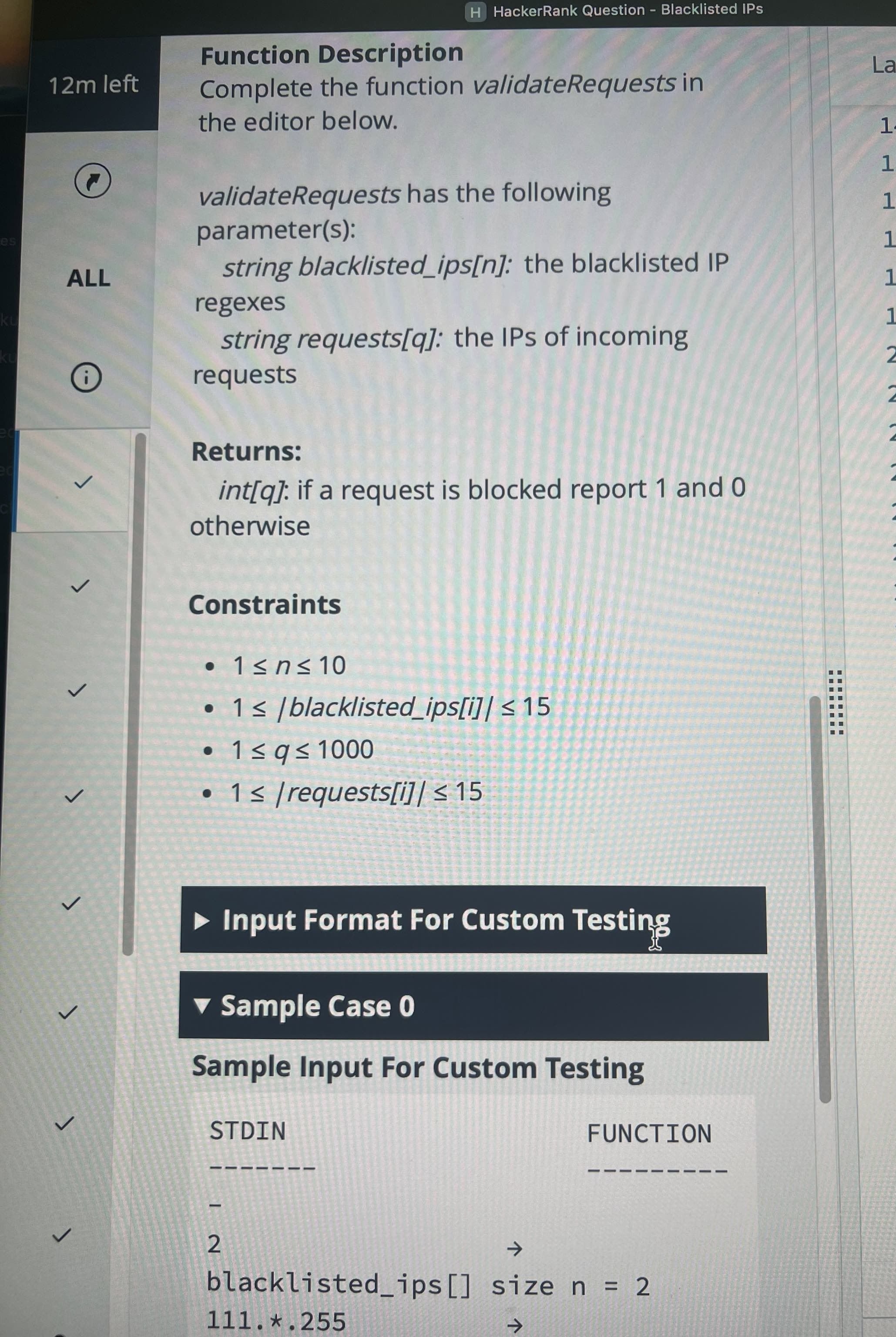
Difficulty Assessment
In my view, this problem is at a Medium difficulty level.
It’s not the kind of question where I can immediately spot the optimal solution. Instead, it has two core challenges I need to handle:
IP regex-style matching:
I need to implement a correct and efficient way to determine whether a request’s IP matches any of the blacklist patterns.
Sliding window rate-limit check:
I must track how many successful requests an IP has made in the past 5 seconds, which requires a clever data structure to manage the time window.
To solve this question properly, I needed a clear understanding of data structures (especially hash maps and queues/deques) and I had to break the problem cleanly into two independent parts.
How I Interpreted the Problem
I broke the problem into two main logical components. A request is blocked (output = 1) if it satisfies either condition:
1. IP Pattern Matching (Regex Block)
Input:
blacklisted_ips (an array of patterns) and the current request[i].
Rule:
If request[i] matches any pattern in blacklisted_ips, the request is blocked.
Key Detail:
The pattern uses a wildcard *.
An IP is made of four dot-separated numbers (A.B.C.D), and * can match zero or more characters.
My Approach:
Since the number of patterns is small (1 ≤ n ≤ 10), I decided to preprocess patterns and simply check each incoming IP against all patterns.
The wildcard logic is simple enough that a custom matcher (or a built-in glob/wildcard match) works well.
2. Rate-Limit Logic (5-Second Window Block)
Input:
The request IP request[i], which arrives at time i.
Rule:
If this IP has at least 2 successful (not blocked) requests in the past 5 seconds then the current request is blocked.
Key Detail:
Only unblocked requests count.
If a request is blocked, it is not added to the future sliding window.
My Approach:
This is the more complex part.
I needed a data structure that stores, for each IP, the timestamps of all its successful requests, and can quickly remove outdated ones (older than 5 seconds).
Linkjob AI worked great and I got through my interview without a hitch. It’s also undetectable, I used it and didn't trigger any HackerRank detection.
If you've never used AI interview assistants on platforms like HackerRank and are concerned about their stealthiness, we recommend reading: HackerRank how to vheat.
Detailed Solution Approach
My final solution revolves around one core data structure and one matching function.
1. Core Data Structure
I used a map to track all successful request timestamps per IP:
SuccessfulRequests: Map<string, Deque<int>>Key: IP address (string)
Value: a deque storing all timestamps of successful (unblocked) requests, in ascending order
The deque makes it easy to pop expired timestamps from the front in O(1) time.
2. is_blacklisted(ip, blacklisted_ips) Function
This function checks whether an IP matches any blacklist pattern.
For every pattern in blacklisted_ips:
I apply a wildcard-matching algorithm (two pointers or recursion both work).
If the language provides a built-in matching function, using that is even simpler.
As soon as one match is found → return true.
If no patterns match → return false.
3. Main Loop (Processing All Requests)
I iterate through all requests requests[i] from i = 1 to q.
For each request:
Step 1: Initialize
is_blocked = falseStep 2: Blacklist Check
if is_blacklisted(request[i], blacklisted_ips):
is_blocked = trueIf true → this request is blocked (output = 1).
Step 3: Rate-Limit Check
Only run this step if not already blocked:
Get the deque for this IP:
times = SuccessfulRequests[ip]Remove stale timestamps:
while times.front < i - 5:
pop_front()If after cleanup, the deque size ≥ 2 → block this request.
Step 4: Final Handling & Update
If is_blocked == true → output 1.
If not blocked:
Output 0.
Add the current timestamp i to SuccessfulRequests[ip].
This ensures:
Only successful requests are tracked.
The sliding window always stays valid.
Both blocking rules are fully satisfied.
At the end, I return the array of 1s and 0s representing all request outcomes.

Multiple-Choice Questions
The multiple-choice questions were in the format shown in the images below, and there were 15 of them in total. I felt that the multiple-choice section was slightly harder than the coding question, roughly at an upper-mid difficulty level.
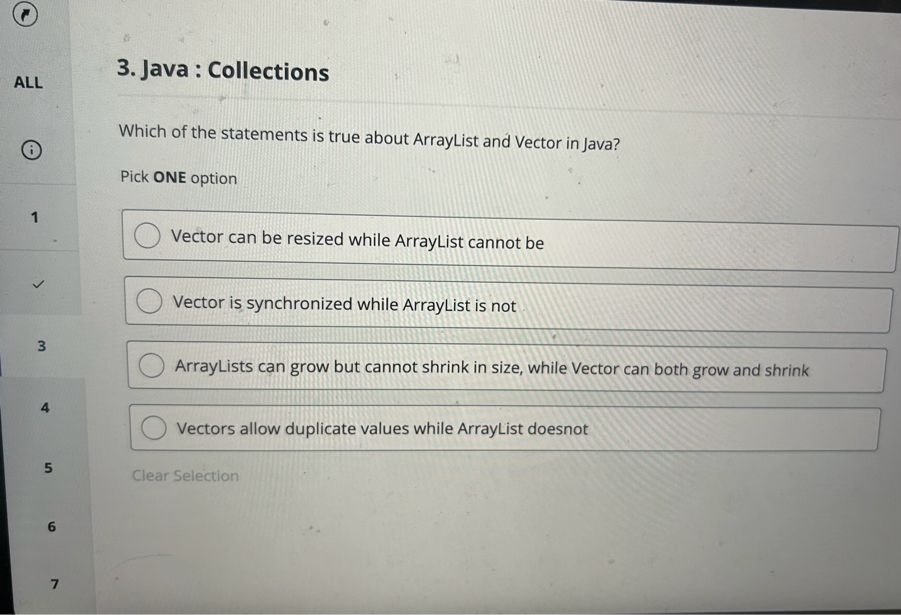
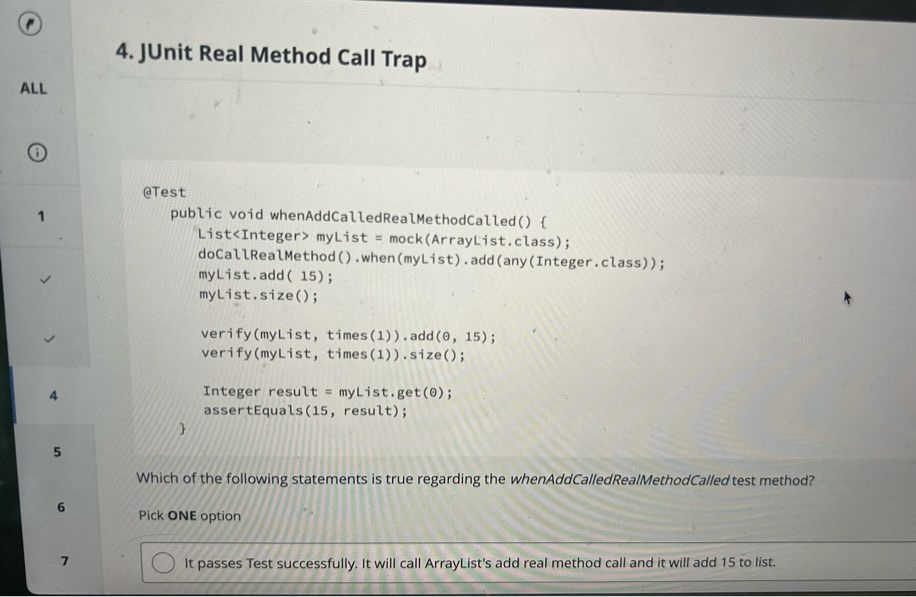
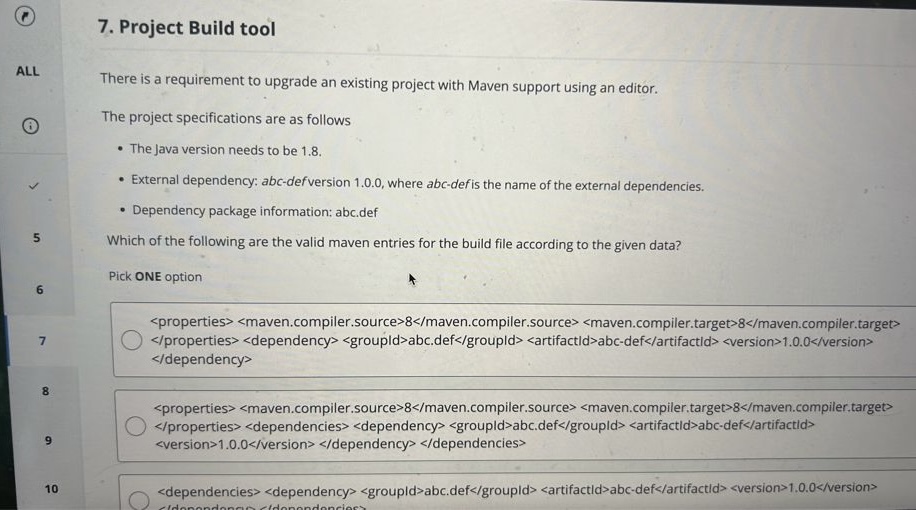
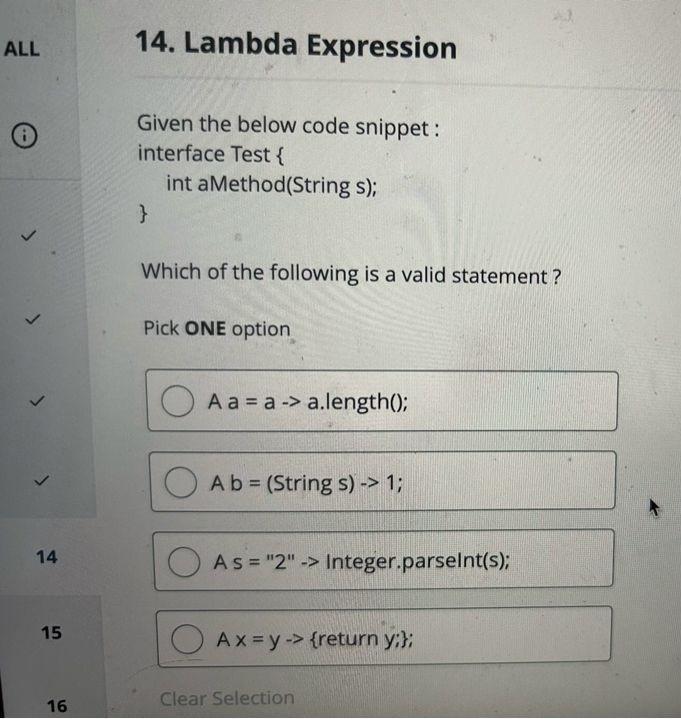
In-Depth Summary of the UBS Assessment Focus
After completing this online assessment (OA), my takeaway was that the test was very clearly designed. Its goal was to comprehensively evaluate whether I possess a qualified engineering mindset and strong system-level problem-solving ability.
In my view, the focus went far beyond core Java knowledge. It delved deeply into areas that are critical in enterprise development, including efficiency, engineering standards, and risk control.
The purpose of this assessment was very clear: to identify professionals who can immediately take on high-standard development work and have a deep understanding of system robustness.
High-Performance Data Structures & Algorithmic Skills
Ability to translate complex business requirements (such as real-time rate limiting and dynamic pattern matching) into efficient algorithmic solutions.
Practical skill in combining and optimizing collection framework components (Map, Queue/Deque) to achieve optimal time complexity in specific scenarios.
Software Engineering Standards & Project Configuration Management
Precise understanding of the structure, tag hierarchy, and parameter scope within mainstream build tools (e.g., Maven) configuration files.
Mastery of dependency management and compiler version settings to ensure portability and consistency across environments.
Foundational Awareness of Concurrency & Thread Safety
Clear understanding of how core Java collection classes behave differently under multithreaded conditions.
Awareness of selecting and applying thread-safe mechanisms proactively to avoid data races when designing systems.
Professional Use of Unit Testing Frameworks
Deep understanding of testing frameworks (such as Mockito), extending well beyond basic syntax.
Ability to identify and apply the appropriate testing strategies to verify complex logic and state changes, ensuring high code quality and coverage.
Adoption of Modern Java Language Features
Proficiency with key features introduced in Java 8 and beyond (such as lambda expressions and functional interfaces).
Ability to write expressive, concise, and maintainable code using modern language capabilities.
UBS HackerRank Test Tips and Strategies
Efficiency First: I aimed for O(N) or better algorithms, avoiding O(N²) brute-force solutions to ensure I passed the performance test cases.
Precise Data Structure Matching: I translated business logic, such as rate limiting and lookups, into the most suitable underlying data structures to maximize code efficiency.
Comprehensive Boundary Coverage: I systematically tested and handled all edge cases, including empty inputs, maximum values, zero-length cases, and critical points in time windows.
Strict Code Standards: I followed function signatures and input/output types precisely, ensuring my implementation matched the problem requirements exactly.
Accurate Configuration Recall: For questions involving build tools or language specifications, I relied on precise memory of configuration structures and API details to aim for full marks.
Rigorous String Handling: When dealing with IP addresses, wildcards, and other string operations, I applied careful logic to avoid subtle errors that could cause incorrect behavior.
Framework Mechanism Priority: For questions involving testing frameworks, I relied on my understanding of the core mechanics of the framework, such as object state changes, to determine correct outcomes.
Modular Logic: Even under time pressure, I tried to break the solution into clear modules to improve debugging efficiency and code readability.
Performance Analysis in Advance: Before coding, I mentally analyzed the time complexity of my approach to ensure it met the performance requirements of the assessment.
Avoiding Unverified Library Functions: When unsure about the performance or side effects of certain library functions, I preferred basic, controllable low-level implementations.
Technical Deep Dive: UBS HackerRank Test Insights
The real value of this UBS online assessment is that it evaluated whether I could translate business requirements into stable and efficient technical solutions. This was not just a test of skills. It was a reflection of my ability to make sound technical decisions.
Efficiency Focused Data Structure Decisions
A core theme of the assessment was its strong emphasis on time complexity. When handling high frequency requests and sliding time windows, every choice had to prioritize efficiency.
Real time performance and amortized cost
I was expected to avoid quadratic or naive linear solutions and instead use structures such as hash maps and double ended queues. These data structures allowed historical lookups to be reduced to amortized constant or logarithmic time. This directly reflected the performance expectations of financial systems, where low latency and high throughput are essential.
Careful resource usage
The combination of IP rate limiting and wildcard matching required me to design solutions that maintained correctness while minimizing unnecessary computation and memory usage.
Risk Control and Code Robustness
In financial services, system stability is a fundamental requirement. The assessment examined my risk awareness through details that may seem small but are extremely important.
Thread safety as a default mindset
I had to treat concurrency risks as a primary design concern. Choosing classes with built in synchronization showed an awareness of defensive programming in multithreaded environments.
Quality assurance through testing
The questions evaluated my understanding of the effects and behaviors of testing frameworks. The goal was to test whether I could use advanced testing techniques to simulate and verify code behavior under various edge cases and realistic scenarios.
Strict Expectations for Engineering Standards
This part focused on my ability to write code that could be integrated smoothly into large enterprise systems involving multiple teams.
Precision in configuration files
The detailed questions about build tool configuration highlighted the importance of accuracy in metadata. Even small mistakes could cause portability issues or build failures across environments, which is a serious problem in enterprise development.
Modern code style and readability
The assessment reviewed my use of modern Java features such as lambda expressions. These features encouraged me to write clean, expressive, and maintainable code that aligned with contemporary engineering practices.
Summary
Overall, the intention of this assessment was to evaluate whether I possess both efficiency driven thinking and a strong understanding of system stability. It tested whether I could make high quality engineering decisions even under pressure.
FAQ
How long is the UBS HackerRank assessment?
The combined time for the MCQs and the coding question was 70 minutes. The timing was quite tight, so if you get stuck on a question, I recommend moving on and coming back to it only if you have time left at the end.
Should I spend more time on coding questions or multiple-choice questions?
In the OA, my strategy was to prioritize the coding questions while still ensuring accuracy on the multiple-choice questions. The coding question sets the upper limit because performance test cases are the main factor for eliminating submissions.
I would first quickly skim through the multiple-choice questions and answer those that relied on memory or standard knowledge, then devote most of my time to the coding question, making sure the logic was correct and the time complexity was optimal.
The knowledge tested in multiple-choice questions was fixed, whereas the coding question required time for design and debugging, so time allocation needed to be weighted accordingly.
See Also
2026 Nvidia HackerRank Test: Questions I Got and How I Passed
How I Cracked 2026 Citadel HackerRank Assesment Questions
My IBM 2026 HackerRank Assessment: Real Questions & Insights
My 2026 MathWorks HackerRank Assessment Questions & Solutions
Questions I Encountered in 2026 Goldman Sachs HackerRank Test

